 In the race to build the most capable LLM models, several tech companies sourced copyrighted content for use as training data, without obtaining permission from content owners.
In the race to build the most capable LLM models, several tech companies sourced copyrighted content for use as training data, without obtaining permission from content owners.
Meta, the parent company of Facebook and Instagram, was one of the companies to get sued. In 2023, well-known book authors, including Richard Kadrey, Sarah Silverman, and Christopher Golden, filed a class-action lawsuit against the company.
Meta’s Bittersweet Victory
Last summer, Meta scored a key victory in this case, as the court concluded that using pirated books to train its Llama LLM qualified as fair use, based on the arguments presented in this case. This was a bittersweet victory, however, as Meta remained on the hook for downloading and sharing the books via BitTorrent.
By downloading books from shadow libraries such as Anna’s Archive, Meta relied on BitTorrent transfers. In addition to downloading content, these typically upload data to others as well. According to the authors, this means that Meta was engaged in widespread and direct copyright infringement.
In recent months, the lawsuit continued based on this remaining direct copyright infringement claim. While both parties collected additional evidence through the discovery process, it remained unclear what defense Meta would use. Until now.
Seeding Pirated Books is Fair Use
Last week, Meta served a supplemental interrogatory response at the California federal court, which marks a new direction in its defense. For the first time, the company argued that uploading pirated books to other BitTorrent users during the torrent download process also qualifies as fair use.
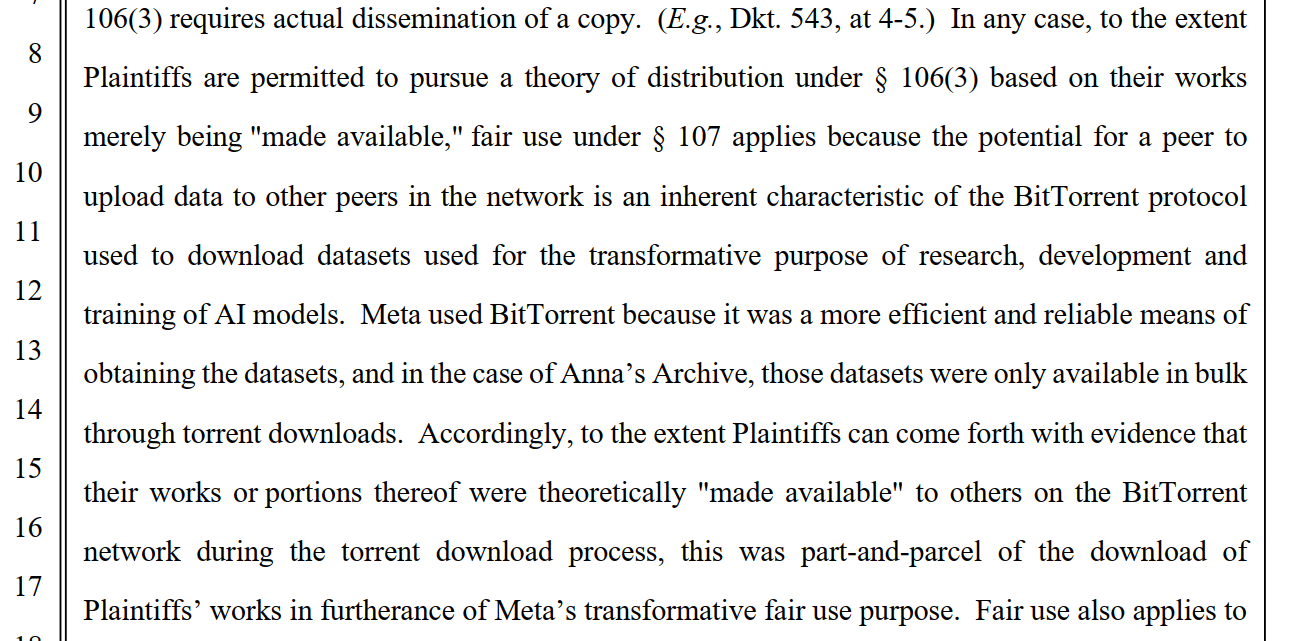
Meta’s reasoning is straightforward. Anyone who uses BitTorrent to transfer files automatically uploads content to other people, as it is inherent to the protocol. In other words, the uploading wasn’t a choice, it was simply how the technology works.
Meta also argued that the BitTorrent sharing was a necessity to get the valuable (but pirated) data. In the case of Anna’s Archive, Meta said, the datasets were only available in bulk through torrent downloads, making BitTorrent the only practical option.
“Meta used BitTorrent because it was a more efficient and reliable means of obtaining the datasets, and in the case of Anna’s Archive, those datasets were only available in bulk through torrent downloads,” Meta’s attorney wrote.
“Accordingly, to the extent Plaintiffs can come forth with evidence that their works or portions thereof were theoretically ‘made available’ to others on the BitTorrent network during the torrent download process, this was part-and-parcel of the download of Plaintiffs’ works in furtherance of Meta’s transformative fair use purpose.”
In other words, obtaining the millions of books that were needed to engage in the fair use training of its LLM, required the BitTorrent up- and downloading, which ultimately serves the same fair use purpose.
Authors and Meta Disagree over Fair Use Timing
The authors were not happy with last week’s late Friday submission and the new defense. On Monday morning, their lawyers filed a letter with Judge Vince Chhabria flagging the late-night filing as an improper end-run around the discovery deadline.
They point out that Meta had been aware of the uploading claims since November 2024, but that it never brought up this fair use defense in the past, not even when the court asked about it.
The letter specifically mentions that while Meta has a “continuing duty” to supplement discovery under Rule 26(e), this rule does not create a “loophole” allowing a party to add new defenses to its advantage after a court deadline has passed.
“Meta (for understandable reasons) never once suggested it would assert a fair use defense to the uploading-based claims, including after this Court raised the issue with Meta last November,” the lawyers write.

Meta’s legal team fired back the following day, filing their own letter with Judge Chhabria. This letter explains that the fair use argument for the direct copyright infringement claim is not new at all.
Meta pointed to the parties’ joint December 2025 case management statement, in which it had explicitly flagged the defense, and noted that the author’s own attorney had addressed it at a court hearing days later.
“In short, Plaintiffs’ assertion that Meta ‘never once suggested it would assert a fair use defense to the uploading-based claims, including after’ the November 2025 hearing, is false” Meta’s attorney writes in the letter.
Authors Admit No Harm, No Infringing Output
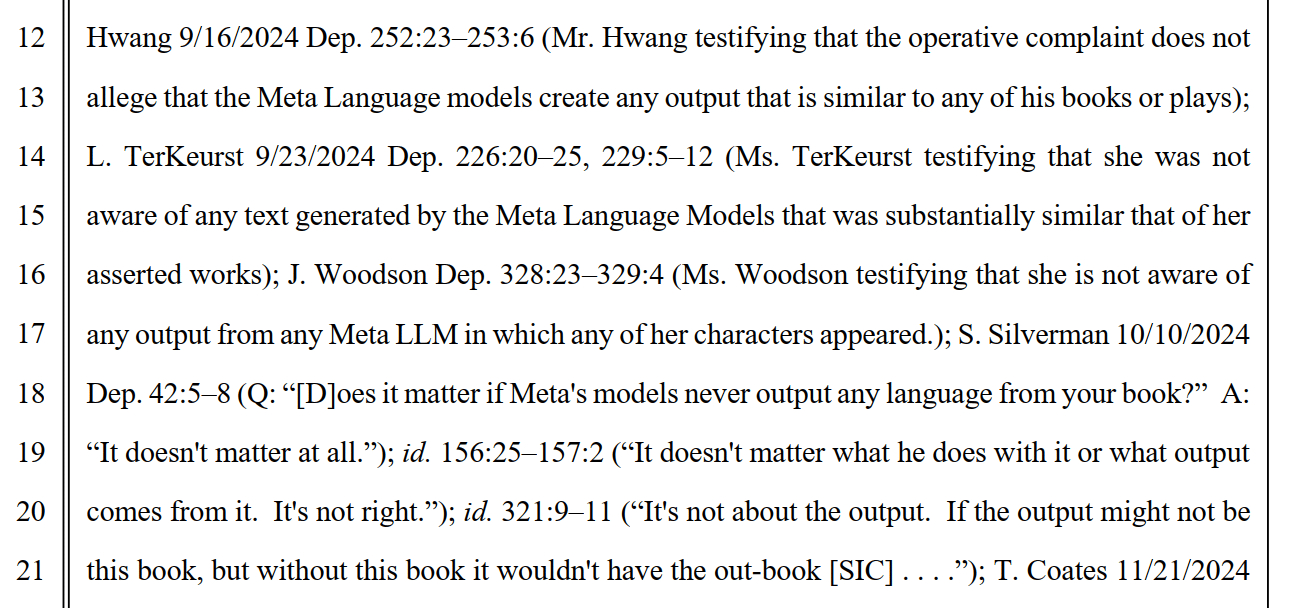
Meanwhile, it’s worth noting that Meta’s interrogatory response also cites deposition testimony from the authors themselves, using their own words to bolster its fair use defense.
The company notes that every named author has admitted they are unaware of any Meta model output that replicates content from their books. Sarah Silverman, when asked whether it mattered if Meta’s models never output language from her book, testified that “It doesn’t matter at all.”
Meta argues these admissions undercut any theory of market harm. If the authors themselves cannot point to infringing output or lost sales, the lawsuit is less about protecting their books and more about challenging the training process itself, which the court already ruled was fair use.
These admissions were central to Meta’s fair use defense on the training claims, which Meta won last summer. Whether they carry the same weight in the remaining BitTorrent distribution dispute has yet to be seen.
‘U.S. AI Leadership at Stake’
In its interrogatory response, Meta added further weight by stressing that its investment in AI has helped the U.S. to establish U.S. global leadership, putting the country ahead of geopolitical competitors. That’s a valuable asset worth treasuring, it indirectly suggested.
As the case moves forward, Judge Chhabria will have to decide whether to allow this “fair use by technical necessity” defense. Needless to say, this will be of vital importance to this and many other AI lawsuits, where the use of shadow libraries is at stake.
For now, the BitTorrent distribution claims remain the last live piece of a lawsuit filed in 2023. Whether Judge Chhabria will allow Meta’s new defense to proceed has yet to be seen.
—
A copy of Meta’s supplemental interrogatory response is available here (pdf). The authors’ letter to Judge Chhabria can be found here (pdf). Meta’s response to that letter is available here (pdf).
From: TF, for the latest news on copyright battles, piracy and more.



